Inside the Web: How 26/11 Exposed the Global Machinery of Terror and Trade
26/11 was more than a terror strike. It revealed a covert web of militant proxies, state handlers, smugglers, financiers, and deniable agents crossing borders and currents. This piece uncovers how those hidden networks converged on Mumbai and what the world must learn from that night.

The Fisherman’s Net
Long ago, on an island at the mouth of three rivers, a fisherman wove a net so fine that no fish could escape.
But each morning when he hauled the net ashore, he found not only fish, but coins, driftwood, torn flags, and sometimes even a dagger. He cursed the river for bringing him strangers’ burdens.
An old monk who lived by the estuary watched him. “Why do you curse the river?” the monk asked.
“It carries filth from faraway lands. My net only wanted fish,” the fisherman said.
The monk replied,
“Your net does not ask what it holds.
The river does not ask whose burdens it carries.
When the strands meet, the whole world is caught.”
Years passed; kings sent their soldiers upriver to seize the fisherman’s net, hoping to trap their enemies before their neighbors did. The same net that once fed a family now ensnared whole villages.
One night, a storm broke the bridges and scattered the boats. The fisherman sat with the monk and asked, “Master, how can I weave a net that catches only what I choose?”
The monk looked at the torn sky and said,
“First know the river.
Then know the hands that pull the ropes.
Until you do, the net will always belong to whoever tugs hardest.”
Lesson: Terror groups, covert agencies, smugglers, and profiteers are strands in the same global net. The river of money, ideology, and covert trade carries them across borders. Unless nations understand both the river’s flow and who holds the ropes, they will remain entangled in each other’s schemes.
SUPPORT DRISHTIKONE
In an increasingly complex and shifting world, thoughtful analysis is rare and essential. At Drishtikone, we dedicate hundreds of dollars and hours each month to producing deep, independent insights on geopolitics, culture, and global trends. Our work is rigorous, fearless, and free from advertising and external influence, sustained solely by the support of readers like you. For over two decades, Drishtikone has remained a one-person labor of commitment: no staff, no corporate funding — just a deep belief in the importance of perspective, truth, and analysis. If our work helps you better understand the forces shaping our world, we invite you to support it with your contribution by subscribing to the paid version or a one-time gift. Your support directly fuels independent thinking. To contribute, choose the USD equivalent amount you are comfortable with in your own currency. You can head to the Contribute page and use Stripe or PayPal to make a contribution.
The Hacked Wifi and the Bomb Blast
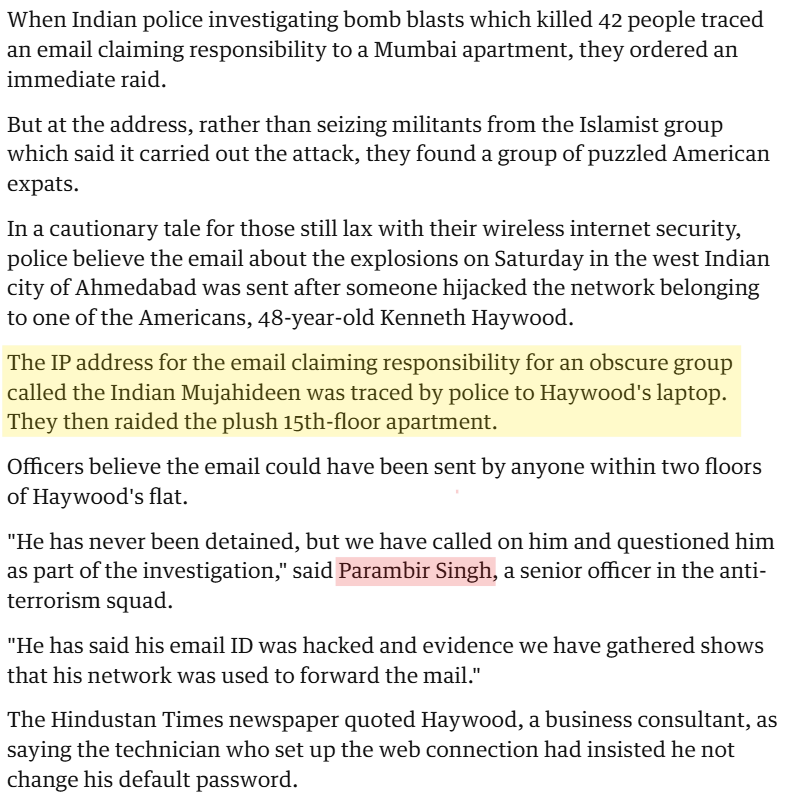
In 2008, as Indian investigators probed a series of bomb blasts in Ahmedabad that killed 42 people, they traced an email claiming responsibility—signed by the Indian Mujahideen—to a Mumbai apartment. Expecting militants, they instead found a group of bewildered American expats.
The email had originated from the network of Kenneth Haywood, a U.S. business consultant, whose unsecured Wi-Fi had been hijacked. Police raided his 15th-floor flat but determined he was not involved.
This bizarre episode highlighted how an American IT consultant's Wifi was used by a jihadi group, showing the vulnerability of unsecured networks. It revealed the murky intersections of terror communications, inexplicable cybersecurity lapses, and transnational investigations before the 26/11 attacks.
As fairy-tale-ish as this claim was, let us understand the landscape better.
Let us meet some actors who make up an interesting cast in the dirty time of bomb blasts and terror attacks in 2008.
Ken(neth) Haywood
- A U.S. national living in Navi Mumbai in 2008; worked in IT/training.
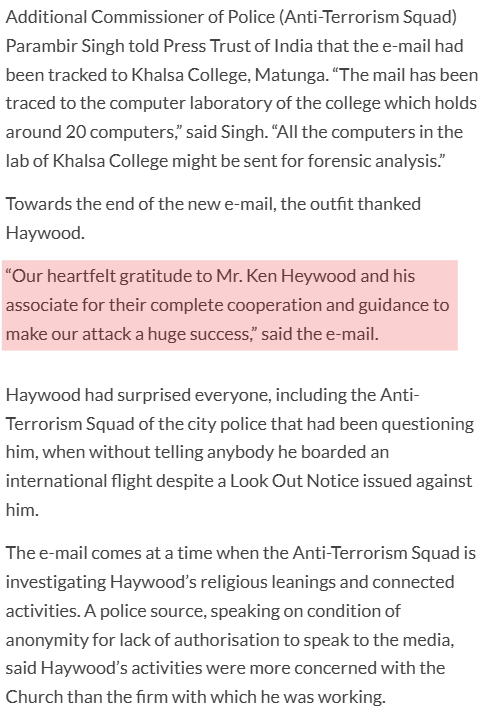
- Minutes before the 26 July 2008 Ahmedabad serial bombings, an Indian Mujahideen (IM) claim-of-responsibility email was sent from the IP address of Haywood’s apartment building. Mumbai ATS said the most likely explanation was Wi-Fi hijacking (an unsecured network). He was questioned, then left India on August 18 despite a lookout notice, returned on September 11, and the ATS later stated that he was not under suspicion (no charges were filed).
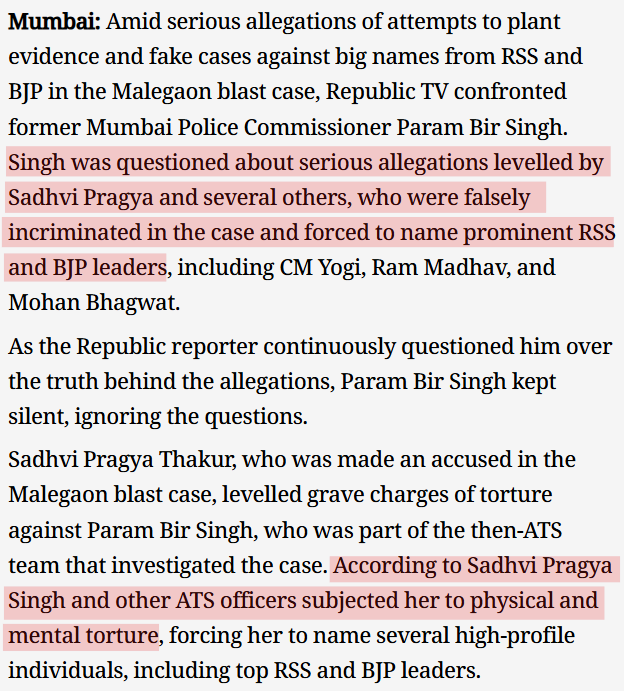
He was given a clean chit by ATS ACP Param Bir Singh.
Mumbai, Sep 12: US national Kenneth Haywood, who left the country while facing a probe in Ahmedabad serial blasts that killed 57 people in Ahmedabad returned to India and presented himself before the Anti-Terrorism Squad (ATS) office in Mumbai on Thursday, Sep 11 to clear his name. ATS' Additional Commissioner of Police Param Bir Singh said that Haywood was no more under suspicion and will be called for statement if a need arises. "As I told you that at this point of time we don't have any suspicion against him as per the enquiries that have been conducted till now. And we don't find need of any narco-analysis," Singh told reporters. (Source: "Ken Haywood declared clean chit by Police" / One India)
Singh has been infamous for being the guy who was at the forefront of the creation of the "Saffron Terror" campaign by the Congress. He was involved in the torture of Sadhvi Pragya.
- IM later sent a taunting follow-up email “thanking” Haywood—police still treated the case as misuse of a third-party connection.
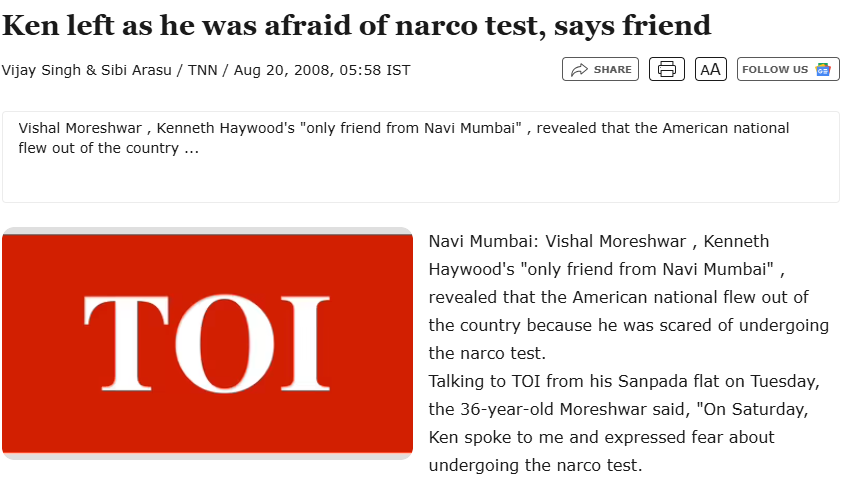
Why did Ken leave India even when there was a lookout notice for him? Because, he didn't want to take the "narco test".
Interesting.
Vishal Moreshwar
- Described in contemporaneous reports as Haywood’s friend (and sometimes “legal adviser”) in Navi Mumbai. He told media Haywood fled because he feared a narco test; he reappeared when he returned to India.
Moreshwar's bio on his own site for his firm Niche Finance says:
Dr Vishal Moreshwar is a seasoned financial advisor with thirty years of experience in bridging capital and trading. From modest beginnings 35 years ago in Sholapur, Maharashtra, has climbed to the position of owning multiple businesses and mentoring a large due diaspora reaching 69 nations worldwide.
Let us put this all together.
An interesting post on X says that Haywood, who was apparently working in IT but couldn't change his WiFi password so terrorists could hack it, was actually a Pastor. What this handle alleges is serious. That Haywood was also in touch with the SIMI operatives.
Before we go forward, let us quickly review the timeline during 2008.
- May–July: Jaipur, Bengaluru, Ahmedabad bombings; IM emails accompany several attacks. Haywood’s IP is used for the Ahmedabad mail; he’s questioned.
- Aug–Sep: Haywood departs and returns; ATS says no suspicion. Separate Delhi blasts in September involve another IM email traced to a different Mumbai IP.
- Nov 26–29: Mumbai 26/11; later investigations tie reconnaissance and planning to Headley/LeT/ISI.
Now, let us move to the third and most important character - David Headley.
That year, 2008, was a watershed in terms of the kind of attacks unleashed on India. Jaipur, Bengaluru, Ahmedabad bombings, Delhi blasts to 26/11. Suddenly, the Indian Mujahideen was everywhere.
While Haywood had a connection with the Ahmedabad bomb blast, anothe American David Headley was the central figure in the preparation for 26/11.
David Headley - the Kingpin
David Headley wasn't alone. He was working with several people within India.
Rahul Bhatt was one of them. Despite evidence, strangely, nothing happened to Rahul Bhatt.
According to the Mumbai Mirror newspaper, Pakistan-born United States citizen Headley's 'Rahul' was apparently Rahul Bhatt, filmmaker Mahesh Bhatt's only son. Headley, who was arrested by the Federal Bureau of Investigation in Chicago last month, is said to have told his interrorgators that he met Rahul Bhatt during one of his trips to Mumbai. (Source: No clean chit yet for Rahul Bhatt: Sources / rediff)
To under Headley better and his work in 26/11, let's understand him via this excellent documentary.
When you watch this Frontline/PBS documentary you see some strange and rather incredible claims from the American intelligence.
- British intelligence (GCHQ) successfully monitored Lashkar’s online communications before the attack, including advanced methods like Voice over Internet Protocol (VOIP).
- There was intercepted chatter indicating a possible attack on Mumbai by sea, which was relayed to Indian authorities, resulting in warnings about the Taj Hotel as a potential target. However, the security measures taken were temporary and insufficient.
- Headley’s communications with Lashkar leadership and ISI handlers—including email exchanges, credit card purchases, and surveillance videos—were not specifically flagged, and his digital trail was missed by spy agencies.
- U.S. officials had intelligence about a Lashkar threat to Mumbai, but the information was disconnected and did not lead directly to Headley.
So, British and American intelligence were "successfully" monitoring the Lashkar operatives. There was chatter of a Mumbai attack. But for some strange reason, there was no flagging of Headley's communication with the Lashkar and ISI handlers.
Really?!
Go figure!
Let's go through his chronology again.
DEA Informant Period (≈ 1997 – Mar 2002)
- Worked under DEA case agents out of New York & Newark on heroin-smuggling cases linked to Pakistan.
- Travelled repeatedly to Pakistan and Europe; his Pakistani passport and fluent Urdu made him valuable.
- DEA says it formally de-activated him March 2002 after concluding a set of heroin prosecutions.
- No public evidence of further DEA payments or direction after that date, though some later inter-agency memos debated whether he had remained a “source of convenience.”
Turn to Lashkar-e-Taiba / Radicalisation (2002 – 2005)
- 2002: reportedly begins attending LeT training camps in Pakistan-administered Kashmir (Daura-Aam, Daura-Khas, weapons courses).
- Builds links with Sajid Mir and other LeT planners.
- Marries again in Pakistan; one wife later warns U.S. embassy in 2005 that he is working with jihadis—warning is logged but not escalated.
- Keeps a foot in legitimate business (visa/immigration consultancy with school friend Tahawwur Rana in Chicago) providing him travel cover.
Operational Bridge – Business Cover & Recon (2005 – 2008)
- Uses Immigrant Law Center / First World Immigration Service (Rana’s firm) as cover for South-Asia and Gulf trips.
- 2006-07: at LeT direction, begins surveillance of Mumbai & other Indian cities—video, GPS, photos of waterfront approaches, hotels, Jewish targets (Nariman House).
- 2007: second wife warns U.S. officials again about his LeT links; report not actioned.
- Runs parallel heroin and hawala contacts in Pakistan/Gulf—classic overlap of criminal profit + jihadist tasking.
- Maintains good standing in U.S. travel system thanks to American passport and business-visitor narrative.
Final Build-Up to Mumbai Attacks (2008)
- Early 2008: delivers detailed target packages to Sajid Mir & LeT ops wing.
- Summer-2008: reports suggest he scouts landing sites and conducts boat-route recce from sea.
- Nov 26-29 2008: Mumbai 26/11 attacks kill 166; Headley is not on-scene—he is the advance scout/facilitator.
- U.S. agencies publicly identify LeT and ISI links; Headley’s role is still undiscovered.
Post-Mumbai Operations & Arrest (2009 – 2010)
- Continues travelling; starts exploring Danish cartoonist attack plot for LeT.
- Oct 3 2009: arrested at O’Hare Airport by FBI JTTF while departing for Pakistan.
- Mar 2010: indicted on 12 counts incl. conspiracy to murder & material support to terrorism; cooperates to avoid death penalty and extradition.
- Mar 2013: sentenced to 35 years in U.S. federal prison.
- 2025: co-accused Tahawwur Rana extradited to India to face trial.
Irrespective of what the US and its establishment would have us believe, the Indian intelligence officials do not believe in the canard that somehow all the evidence and the overlaps were either missed or were coincidental.
The former Indian Home Secretary GK Pillai articulated it very clearly.
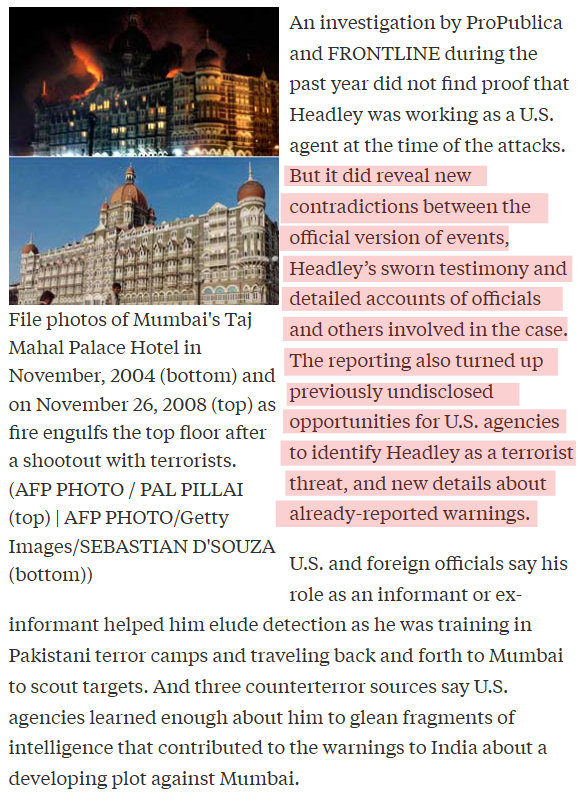
During an interview in Delhi, former Indian Home Secretary G.K. Pillai asserted that U.S. authorities know more about Headley than they have publicly stated. Several senior Indian security officials said they believe that U.S. warnings provided to India before the Mumbai attacks came partly from knowledge of Headley’s activities. They believe he remained a U.S. operative. “David Coleman Headley, in my opinion, was a double agent,” said Pillai, who served in the top security post until this past summer. “He was working for both the U.S. and for Lashkar and the ISI.” (Source: "The American Behind India’s 9/11 – And How U.S. Botched Chances to Stop Him" / Propublica)
This understanding became even stronger after his sentencing.

Recon + cut-outs. David Coleman Headley (U.S. citizen of Pakistani origin) conducted multi-round reconnaissance for Lashkar-e-Taiba (LeT), using business/NGO cover tied to Tahawwur Rana. He pled guilty in U.S. court (2013) and received 35 years; Rana was extradited to India in 2025. These are hard facts from U.S. DOJ/State/AP/Reuters.
Handler ecosystem. Headley’s trajectory included periods as a DEA source, then deepening links to LeT/ISI as he scouted Mumbai targets—showing the classic “crossover” risk when criminal/intelligence equities blur. (ProPublica/PBS investigative work compiles this record from interviews, files and court materials.)
Hawala / informal value transfer. FATF and allied bodies have long flagged hawala/HOSSPs as resilient rails for terror finance; Gulf–South Asia corridors are repeatedly cited. Treat these as the default plumbing under many South Asian jihad ops.
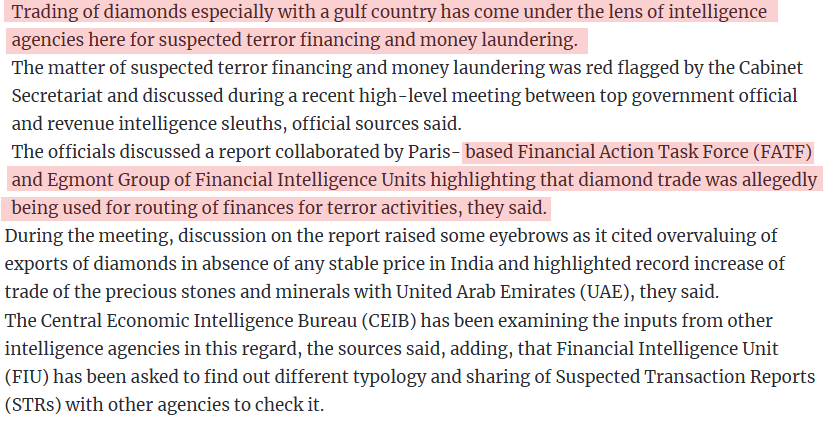
Trade-based laundering (TBML). Diamonds/gold and other high-value, high-mobility commodities are classic TBML vehicles—valuations are subjective, chain-of-custody is opaque, and routing often spans Dubai–Antwerp–Mumbai/Surat. FATF/Egmont, FinCEN, EU risk notes, and industry analyses document the sector’s vulnerability to ML/TF (without asserting a specific case unless proven).
The FATF and the Egmont Group of Financial Intelligence Units collaborated on a typologies research project to identify the money laundering and terrorist financing (ML/TF) vulnerabilities and risks of the “diamond pipeline”, which covers all sectors in the diamond trade: production, rough diamond sale, cutting and polishing, jewellery manufacturing and jewellery retailers. (Source: Money laundering and terrorist financing through trade in diamonds / FATF)
Reality check: Modern FATF work also cautions that, while TBML is a major ML risk, evidence tying TBML directly to specific terror acts is uneven; most countries don’t consistently detect TBML used to finance an attack (as opposed to general criminal ML).
Interestingly, Pakistan had sent 30 questions to India on the Mumbai Attacks along with two supplementary questions. They were dismissed as an "attempt to shift the blame to India". However, one question is quite interesting.
First question was about a Surat based Diamond merchant who also had alleged links with Karachi, and according to Pakistan government, may have provided the funding for the Mumbai attacks. The intention was clearly to prove that there is some home grown connection to the Mumbai attacks. (Source: Pak says Surat diamond merchant funded Mumbai attacks; India trashes it / India Today)
Diamond trade from Surat to a Gulf country - UAE? - has been used for terror financing and money laundering.
So what does this all point to? That 26/11 was far more complex than we have come to understand.
Why 26/11 looks like an intelligence marketplace, not just a terror strike
Multiple interests converged in the orchestration of the 26/11 attacks. Intelligence agencies, terror outfits, transnational crime syndicates, and clandestine networks (each with its own motives) coalesced to plan, prepare, and execute the assault. It was not merely a singular group’s operation but a web of actors exploiting shared goals: disruption, fear, and strategic advantage.
This convergence created a sophisticated blueprint, combining local facilitators with global enablers, making the attacks devastatingly effective.
The incident highlighted how overlapping criminal, ideological, and geopolitical agendas can converge into a lethal campaign when coordination and opportunism intersect.
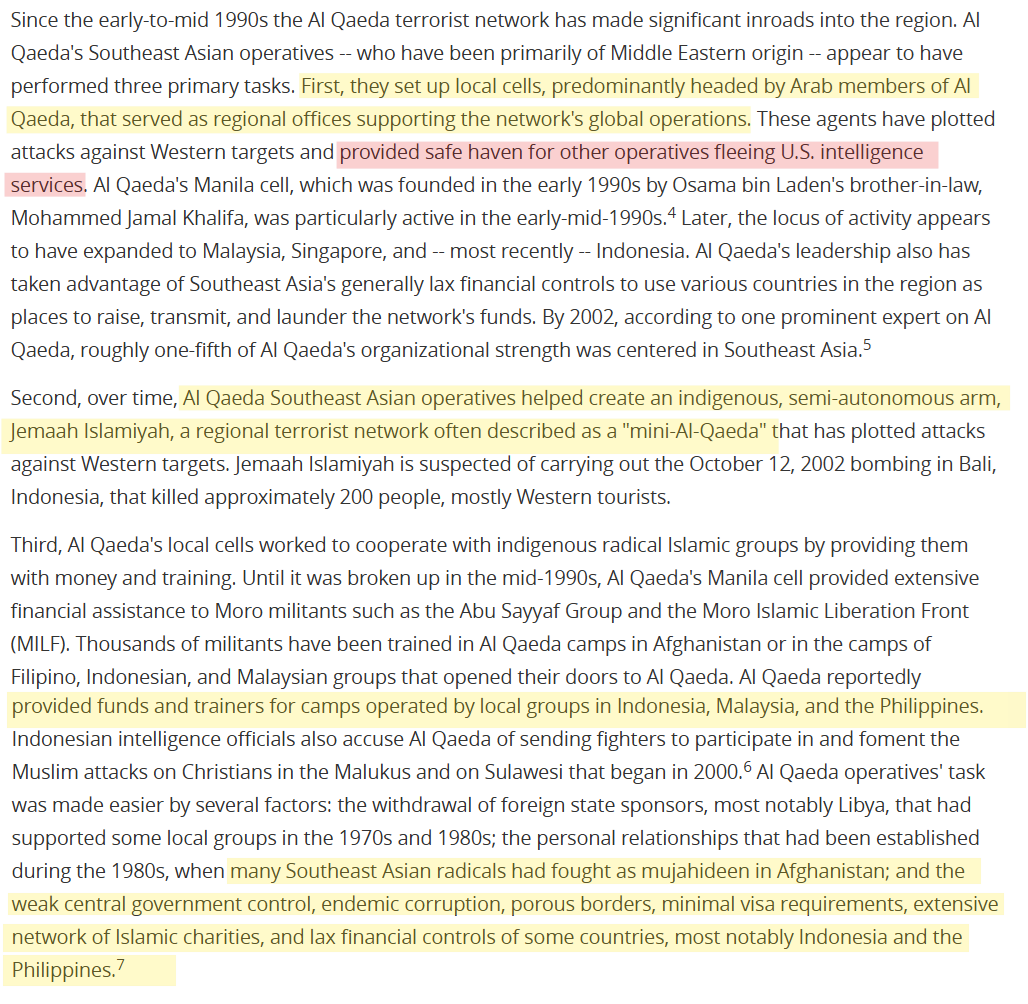
- Deniable assets with overlapping masters. David Coleman Headley’s trajectory demonstrates how one individual can navigate three worlds that are typically treated as distinct — crime, terrorism, and intelligence. In the 1990s, operating under his birth name Daood Gilani, he was arrested for heroin trafficking on the Pakistan-US route. He avoided a long sentence by becoming a confidential source for the U S Drug Enforcement Administration. As a DEA informant, he learned the mechanics of covert travel, cultivated smugglers’ networks, and gained the trust of case agents who valued his access to South-Asian drug pipelines.
- Cross-border “visibility bargains.” Western services gleaned value from debriefing such travelers; simultaneously, Pakistan-based handlers exploited the same corridors. Open-source hearings after 26/11 (U.S. Senate) focused on the multi-agency coordination gaps that let those seams persist.
- Commodity/route arbitrage. Independent of any one plot, diamond and gold pipelines (Surat/Dubai/Antwerp) are empirically high-risk for ML/TF; if jihad-aligned fixers also touch narcotics and smuggling lanes, you get the “shadow economy” that can bankroll travel, safe houses, and recon for operations like 26/11—even if each rupee/dollar can’t be courtroom-traced to the attack.
Implication: Think of 26/11 as a “collision point” of networks: jihad logistics, criminal finance, and competing intelligence harvesting—each extracting value while amplifying systemic risk.
26/11 was not just LeT’s operation; it was a junction of three economies: a jihad logistics economy (handlers, couriers, safe houses), a criminal finance economy (hawala, TBML through diamonds/gold), and an intelligence economy (deniable assets who moved value and information across borders).
Headley’s career demonstrates how these economies overlap: informant-turned-operative, business cover, and multi-jurisdictional reconnaissance.
The lesson for states is uncomfortable—intelligence gains harvested from criminal pipelines are never free; they create cut-outs and loyalties that evade the control of any single agency.
The fix is not just better policing of terrorists, but joint disruption of the commercial and financial rails that let such hybrid networks regenerate.
Now, when you look at this post on X, it seems extremely intriguing in terms of what it conveys.
This post alludes to a larger network that Headley had and what he set in motion via his activities.
Headley’s operations functioned as a covert exploration of the geopolitical corridors linking Central Asia, Pakistan, and India, using the façade of legitimate business and non-governmental activities. His movements effectively “opened and tested” these routes, providing a template for intelligence and substate networks to navigate and exploit regional pathways under plausible civilian cover. Through his dual identity as both entrepreneur and operative, Headley symbolized the convergence of private enterprise and clandestine reconnaissance that defined post-9/11 intelligence experimentation in South and Central Asia.
For Western intelligence debriefers, such deniable travelers were invaluable sources of regional insight. They gathered situational awareness on Taliban and Al-Qaeda movements without the formal visibility of traditional espionage. By embedding informants in commercial or NGO structures, Western agencies could maintain proximity to insurgent transit routes while avoiding diplomatic repercussions—a strategic adaptation to the blurred boundaries between counterterrorism and covert influence operations.
Meanwhile, Russian intelligence services, particularly the FSB and GRU, maintained deep surveillance networks across Central Asia. Their HUMINT and SIGINT coverage was robust enough to monitor not only local militant flows but also Western intelligence piggybacking on the same channels. This awareness allowed Moscow to convert its intelligence advantage into diplomatic and geopolitical leverage, using exposure or selective cooperation as a bargaining tool against both regional rivals and Western powers.
The cumulative result of these overlapping covert activities is a toxic feedback loop. Shared or dual-use assets, private profiteering from narcotics and contraband, and layers of cutouts eroded the boundaries between state policy and organized crime. Each actor’s pursuit of influence and intelligence inadvertently intensified instability, creating a cycle in which geopolitical maneuvering, black-market economics, and counterterrorism blurred into a single, self-reinforcing system of covert dependency.
We will also look at another X thread that we have downloaded as a PDF. This seems extremely random at first, written by an unknown author, but its content reveals many confirmed patterns. (PS: we don't endorse the author/handle or his content in general, but we have tried to look in to the veracity and plausibility of the content in this thread)
We will parse out its content and discuss it below to get a better understanding of events connected to 26/11.
Here is the PDF for the reader's benefit.
The fundamental assertion of the thread is:
The Southeast Asian Corridor of Terror
Sri Lanka’s position in the Indian Ocean makes it a natural crossroads for legal shipping as well as illicit flows. The Transnational Crime in Sri Lanka report highlights how that geography has historically drawn smuggling networks to its ports and coastlines.
The country has been cited as a waypoint for arms consignments bound for conflict zones, for irregular migration and human-trafficking routes linking South Asia, the Gulf and Southeast Asia, and for other contraband that rides the same maritime lanes. The study examines these general criminal corridors rather than any single ideological network, but it makes clear that Sri Lanka’s exposure is structural: its busy sea-lanes and lightly monitored feeder ports make it an attractive staging and refuelling stop. That vulnerability means that even when the flows are not jihad-linked, the infrastructure comprising boats, crews, brokers, informal finance remains available to be tapped by extremist or armed actors seeking discreet transit across the region’s waterways.
The “Maldives: Extremism and Terrorism” country profile points to the emergence of small but visible jihadist currents inside the island nation. It highlights individual figures such as Ali Assham, described in open reporting as having ties to Lashkar-e-Taiba (LeT), and notes how certain mosques and prayer circles became informal hubs for ideological outreach and recruitment. There is clear evidence of how LeT has made strong inroads into the Maldives.
There is confirmation that the ideological and human-recruitment dimension of South-Asian jihadist movements has penetrated the island deeply. As per the Maldives' own President Nasheed, some Maldivians did play a role in the Mumbai Attacks of 2008.
Since the early 2000s, young Maldivians have gone to Pakistan to join the ranks of Lashkar-e-Taiba (LeT), an extremist group that has ties to Pakistan’s Inter-Services Intelligence (ISI). While some Maldivian nationals in Pakistan were funneled into Afghanistan to support the jihad, others were sent to India to carry out attacks. In 2008, Maldives national Ali Assham was reported to have been involved in the LeT-linked 2008 attack against the Indian Institute of Science in Bengaluru, and according to former President Nasheed, undisclosed Maldivians were thought to have played a role in the 2008 Mumbai terrorist attacks. Those Maldivians who were extremely susceptible to radicalization in Pakistan and Afghanistan were reported to have allegedly traveled to Iraq and Syria to join extremist groups such as ISIS and the al-Qaeda linked al-Nusra Front. Media reports suggest that over 200 to almost 300 Maldivians have joined these terrorist groups. The figures suggest that about 1 in every 1,500 Maldivians becomes a terrorist fighter. (Source: Maldives: Extremism and Terrorism / Counterterrorism Project)
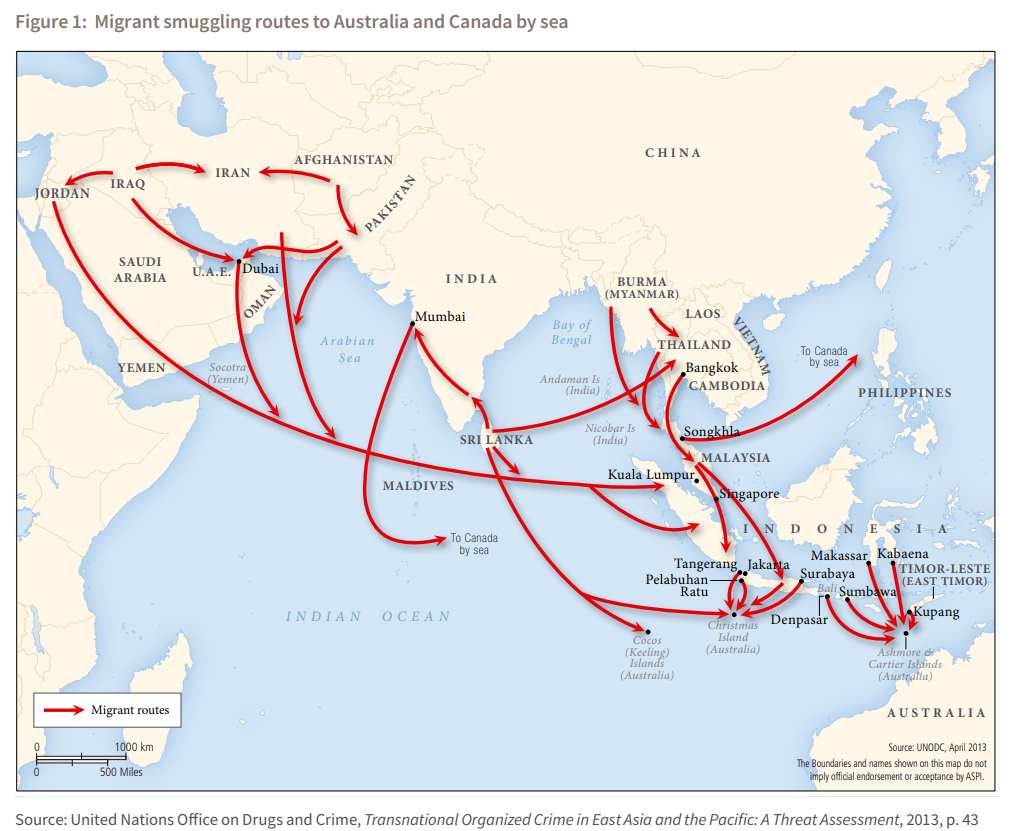
A separate UNODC study on Maritime and Organized Crime in the Eastern Indian Ocean documents the entrenched smuggling and trafficking networks that link Sri Lanka, the Maldives and neighbouring coastal states.
These routes service a spectrum of illicit trade — from fuel, drugs and people to wildlife and small arms — moving along traditional fishing channels and feeder ports that lie outside the radar of major customs hubs.
This image illustrates the network and the movements of drugs. The entire network runs the narco-terror trade as well.
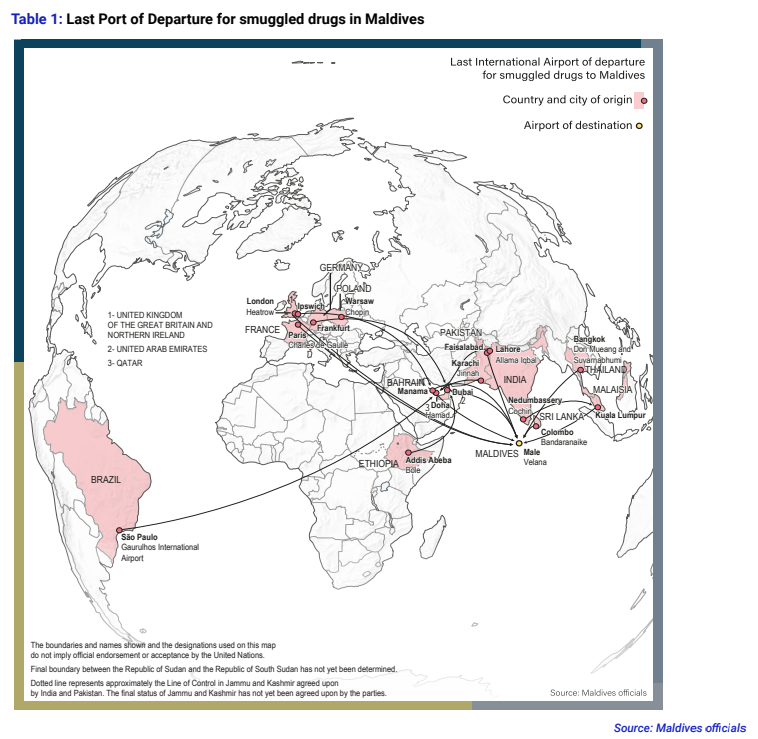
Taken together, three elements stand out. Sri Lanka has long functioned as a transit and contraband node in the region.
The Maldives has shown evidence of jihadist ideological penetration and some LeT-linked recruitment. And the wider Indian-Ocean / Eastern Indian-Ocean corridor is criss-crossed by agile, low-volume trafficking flows that can be co-opted or rented by militant networks when needed.
Due to the region's geography — dense maritime traffic, island proximity, interconnected ports, and fishing routes — the Indian Ocean naturally presents latent corridors for clandestine movement. These under-governed waterways are well-suited for small-scale transfers of people, arms, or dual-use components that can evade routine inspection.
SEA/Colombo/Bangkok Jihad Corridor
Jemaah Islamiyah and related Southeast Asian jihad networks utilize the corridor running through Singapore, Malaysia, Indonesia, southern Thailand, and into the Indian subcontinent via Colombo and Bangkok, for several operational functions:
- Movement of operatives and facilitators: Weak border security in the region allows transit between militant group cells, with Thailand, Singapore, and Malaysia playing host to sleeper cells or facilitators, and links further west to South Asian and Gulf-based radical financiers.
- Resource sharing: Alliances with other networks like Manila's Moro Islamic Liberation Front (MILF) allow JI and AQ affiliates to share training, arms procurement, and financial support; often, these corridors are also used to move weapons and technical material needed for attacks.
- Financial flows: The corridor is leveraged for illicit commerce and clandestine money flows, especially by exploiting trade linkages between South Asia, the Gulf, and Southeast Asian states with significant Muslim populations and remittance flows.
Commodity and TBML Rails
Terrorist financiers and criminal syndicates use TBML—the laundering of funds through manipulated trade invoices and over- or under-valued shipments—to obscure both the origins and destinations of money:
- Diamonds and gold: The precious stones and metals industry is highly vulnerable to TBML, regularly used to launder and move funds. Synthetic stones and gold are over-invoiced, with shipments rerouted through major trade hubs like Hong Kong, Dubai, and Singapore, masking illicit flows under legitimate business activity. Examples include the 2023–2025 India–Hong Kong synthetic diamond ring, exploiting SEZs and fraudulent export invoices to move nearly $65 million in illicit funds.

- Other commodities: Solar panel trade, electronics, and other sectors are also exploited, with front companies utilizing fake paperwork to move money and evade scrutiny, especially in Pakistan and the wider Gulf region.
Hawala Networks
Hawala is an informal, trust-based system of remittance and value transfer that bypasses formal banking regulations:
- Used for remittances and terror finance: Hawala networks layered into legitimate business channels are routinely employed to transfer funds for jihadist networks, charitable fronts, and madrasas in India, Pakistan, and the Gulf.
- Links to Dubai: Dubai functions as a critical regional finance center, hosting thousands of South Asian trading companies that settle accounts between hawala brokers, with extensive use by Iranian, Pakistani, and Gulf sponsors of terror finance.
- Regulatory challenge: Hawala’s structure is highly resistant to tracing and oversight; as a result, charities with Gulf-based donors often channel money to extremists or radical seminaries in Kashmir using such underground rails.

David Headley and Network Contact
David Headley (Dawood Sayed Gilani) is documented to have worked with Lashkar-e-Taiba (LeT) and the Brigade 313 network of Ilyas Kashmiri, conducting surveillance support and attack planning across India, Denmark, and the wider region:
- Contact points: Headley was instructed and enabled by senior facilitators in Pakistan, met with Brigade 313’s Ilyas Kashmiri in Waziristan, and worked with LeT’s Abdur Rehman Syed for operational support, including funding and logistics for attacks in Mumbai and Denmark.
- Financial and travel rails: While Headley’s documented financial support primarily came from LeT and Brigade 313’s dedicated channels, there is indirect overlap with the TBML and hawala networks, especially in travel and movement of funds and personnel through regional corridors tied to SEA jihad infrastructure.

If Headley or his handlers had cultivated access or alliances within these maritime channels, it would have expanded their strategic reach for support activity, exfiltration or logistics beyond the immediate Mumbai operation. Yet the absence of concrete attribution in open-source records means such utilization remains a working hypothesis rather than an established fact.
What we do know for sure is that David Headley had researched the sea-route option during his visit to India. This was based on his meeting with possibly a "frogman from the Pakistani Navy."

This comes from the Interrogation Report of David Headley.
Next, we will move on to Central Asia and examine how different powers are working behind the scenes to exert control there. Before we go in, read this very intriguing post.
Central Asia is no desert backwater , it is the new chessboard of global power. Turkmenistan’s Galkynysh gas currently feeds China, but projects like the TAPI pipeline (Turkmenistan–Afghanistan–Pakistan–India) threaten to break Beijing’s grip. A functioning Trans-Afghan corridor… https://t.co/bCvXP22KSF
— रुद्राक्ष📿 (Rudy) (@manamuntu) October 4, 2025
Central Asia: From Periphery to Pivot
Central Asia is a meeting point for many Islamist terror organizations and groups.
Central Asian terror networks increasingly operate as part of a web of alliances and rivalries, with both LeT and Al-Qaeda maintaining ties to local and transnational actors. Their connections center on shared ideology, logistical routes, and overlapping recruitment pools, making the region a persistent source of radical actors and exportable violence. These groups exploit ungoverned spaces, weak border controls, and social grievances, representing a complex threat to security across Eurasia and beyond
With recruitment, fundraising, and operations extending to Afghanistan, Iraq, Central Asia, Europe, Africa, and Australia, LeT has rapidly become a formidable global threat. Today, LeT has close ties with al-Qaeda in Pakistan and supports the Afghan Taliban’s military operations (despite the divide between the two groups’ interpretations of Islam). It also closely collaborates with Jamiat al-Dawa al-Quran wal-Sunna, a Wahhabi group based in the Kunar Province of Afghanistan, in operations against American troops in Afghanistan’s Korengal Valley. These remain only the latest in a long line of hostile activities—most of which have remained sub rosa—affecting U.S. citizens, soldiers, and interests. (Source: "The Menace That Is Lashkar-e-Taiba" / Carnegie Endowment)
Once dismissed as a distant backwater, Central Asia now sits at the heart of Eurasia’s terrorism, trade, energy, and security rivalries.
Pipelines and railways may appear to define the region’s future, yet they are merely the surface architecture of a far deeper geopolitical contest—one driven by control over chokepoints, mineral corridors, and covert influence.
Strategic Corridors and Energy Leverage
Turkmenistan’s clout stems from the giant Galkynysh gas field, today piped mainly to China via the Central Asia–China Gas Pipeline. Beijing’s near-monopoly faces a challenge from the stalled but persistent TAPI line (Turkmenistan-Afghanistan-Pakistan-India).
Should TAPI advance despite Taliban turbulence, Turkmenistan could diversify exports southward, forcing China to concede on price and transit terms across the region.
For Uzbekistan, the priority is to escape its dependence on Russian-controlled northern routes.
Uzbekistan primarily trades with Russia through the Northern Corridor, which uses railways and roads that pass through Kazakhstan. However, recent Western sanctions on Russia have prompted Uzbekistan to seek new, diversified trade routes that bypass Russian territory, such as the Trans-Caspian International Transport Route (Middle Corridor).

Its UAP railway—Uzbekistan-Afghanistan-Pakistan—seeks a southern outlet to the Arabian Sea through Gwadar or Chabahar. Success would tether Uzbek exports to maritime networks independent of Moscow’s grip over Caspian shipping.
Chokepoints and Fragile Security
Tajikistan’s mountain corridors, especially the Pamirs and the Wakhan strip, act as narrow gateways from Afghanistan into Xinjiang. These passes carry not just legitimate cargo but also lithium ore, uranium, and narcotics—making control over them a high-stakes contest for governments, militants, and smugglers alike.
The August 2025 Panj River clash exposed just how vulnerable these lifelines remain to Taliban raids and cross-border militant incursions—risks that can instantly chill investment in both rail and pipeline ventures.

An armed clash occurred on August 24, 2025, between Tajikistan border forces and Taliban fighters near the Panj River, which serves as a border between the two countries. The incident, which took place in the Dovang area of Afghanistan's Badakhshan province, stemmed from a dispute over Chinese mining companies and the destruction of the Panj riverbed, according to Азия-Плюс.
A Taliban militant was reportedly killed in the conflict, and subsequent meetings were held between Tajik border guards and Taliban representatives to discuss the mining activities.
Covert Influence and Intelligence Rivalries
References to MI6 and Germany’s BND evoke the early-2000s Western effort to nurture anti-Russian elements in Uzbekistan after the Andijan massacre (2005), a gambit to chip away at Moscow’s transit dominance. As Europe retreated after the Taliban’s 2021 return, China stepped in—financing infrastructure while quietly positioning itself to oversee uranium- and lithium-rich routes via Chabahar and Gwadar.
China and Expansionist Agenda in Tajikistan
The so-called “Xinjiang nuclear scare” can be read as a pretext for Beijing to expand its security footprint in Tajikistan under the banner of non-proliferation.
China leveraged environmental and radiological concerns over Soviet-era uranium tailings in northern Tajikistan—particularly at Taboshar, Degmay, and the Vakhsh Valley—to justify expanding its border monitoring and security presence during the 1990s and 2000s. International agencies began warning about the hazards these radioactive waste sites posed to the Syr Darya watershed, heightening anxiety about broader regional contamination. Beijing seized on these warnings, citing risks of cross-border water and windborne contamination reaching Xinjiang. These arguments supported demands for joint environmental inspections and improved border infrastructure along the upper Amu-Darya and near the Pamir mountains, with Chinese-language media describing the region as a “radiation belt near China’s western gate”.
Territorial and Security Agreements: In 2011, a key boundary deal saw Tajikistan cede approximately 1,158 square kilometers of sparsely populated Pamir territory to China, settling a long-standing claim dating back to the Qing dynasty era. Dushanbe presented the agreement as the resolution of a historical dispute. In contrast, Beijing emphasized its removal of a “buffer zone” that, left unaccounted for, might threaten Xinjiang’s stability. Between 2016 and 2021, China began funding and staffing small People’s Armed Police posts in Tajikistan’s Gorno-Badakhshan region, near the sensitive Wakhan Corridor. The stated rationale focused on countering terrorism and preventing nuclear material smuggling, but these outposts built upon the narrative that insecure uranium waste and porous borders created a shared threat. This framing helped China gain local and international legitimacy for its security role.
Strategic and Economic Motives: The Wakhan-Pamir corridor, where these Chinese posts appeared, is also of immense strategic value. It provides access to key passes connecting China, Afghanistan, and Central Asia—pathways vital for future energy and transportation links. Furthermore, the zone sits atop substantial deposits of rare earths, gold, and uranium, making resource security a critical driver. Many analysts contend that the “nuclear-waste hazard” narrative served as a non-provocative pretext for deeper goals: bolstering the buffer depth between Xinjiang and the unstable Afghan/Badakhshan regions, securing resources, and implementing preemptive counter-terrorism measures following the rise of unrest in Xinjiang between 2009 and 2014. These interests aligned with China’s Belt and Road Initiative ambitions, positioning roads and pipelines through the corridor.
Meanwhile, the US retains intelligence outposts in Uzbekistan and Kyrgyzstan, intent on preventing any single power—especially China or Russia—from gaining uncontested sway.
26/11: More Than a Terror Attack
The November 2008 Mumbai carnage was not an ordinary terrorist incident.
It was an Act of War.
Its purpose was to paralyse India’s commercial capital, undermine investor confidence, and humiliate the state — an act of war by military-trained proxies.
The attacks also exposed the ecosystem that sustained LeT beyond Pakistan: Gulf-based donors and hawala couriers, diaspora charities, maritime facilitators on the Karachi–Mumbai arc, and cyber-media handlers who issued real-time instructions from Pakistan.
David Headley’s reconnaissance trips, camouflaged as business travel, revealed how cut-outs and front companies allow operatives to move money, people, and intelligence undetected.
26/11 showed that terror logistics, organised-crime supply chains, and intelligence equities were entangled. Headley—once a DEA informant—embodied that overlap, fuelling suspicions in India that elements of Western agencies either missed or mismanaged a potential asset turned terrorist.
For Moscow, which had long tracked jihad pipelines through Central Asia, the attacks underscored how Western “deniable” sources could become liabilities.
For India’s security establishment, the siege was a wake-up call: urban targets could be held hostage for days by state-backed jihadist commandos, not just bombers.





Comments ()